WhatsApp Implements Optional "Strict Account Settings" Mode for Increased Security

WhatsApp has announced a new setting called Strict Account Settings that increases security against sophisticated threats, similar to Apple's Lockdown Mode or Android's Advanced Protection mode.
The mode reduces WhatsApp's attack surface by disabling certain features that can be vulnerable to exploitation. The feature is being rolled out gradually, so don't worry if the setting doesn't appear for you yet.
The setting forces two-factor authentication for your account and forces on security notifications for when a contact's security code changes.
End-to-end encrypted backups are "encouraged" (whatever that means) for users with this setting enabled. I haven't been able to test it out because the setting isn't available to me so unfortunately I can't testify how that works. Normally, E2EE backups are optional, meaning that Meta has access to your messages if you or one of your contacts decides to do an unencrypted backup.
Media and attachments are blocked for unknown senders and link previews are disabled. This is similar to what Apple does in their Messages app when Lockdown Mode is enabled. The "block unknown account messages" setting is also enabled, although it doesn't block all unknown messages, just "high volume" ones.
You won't be able to receive calls from unknown numbers either, and your IP address will be hidden during calls.
Information in your profile such as the last time you were online, photo, about section, and links in your profile will be locked to contacts-only as well.
And finally, no one will be able to add you to a Group unless they're on your contacts list or they're part of a "pre-established, more-selective list of people."
Mostly, the setting is forcing already-existing settings to be enabled, but I view it as a good thing. It could be a stepping-stone toward these being enabled by default sometime in the future.
WhatsApp has also been cooking up a Rust version of their wamedia library that strips metadata and checks to make sure media is conformant to the media format it purports to be.
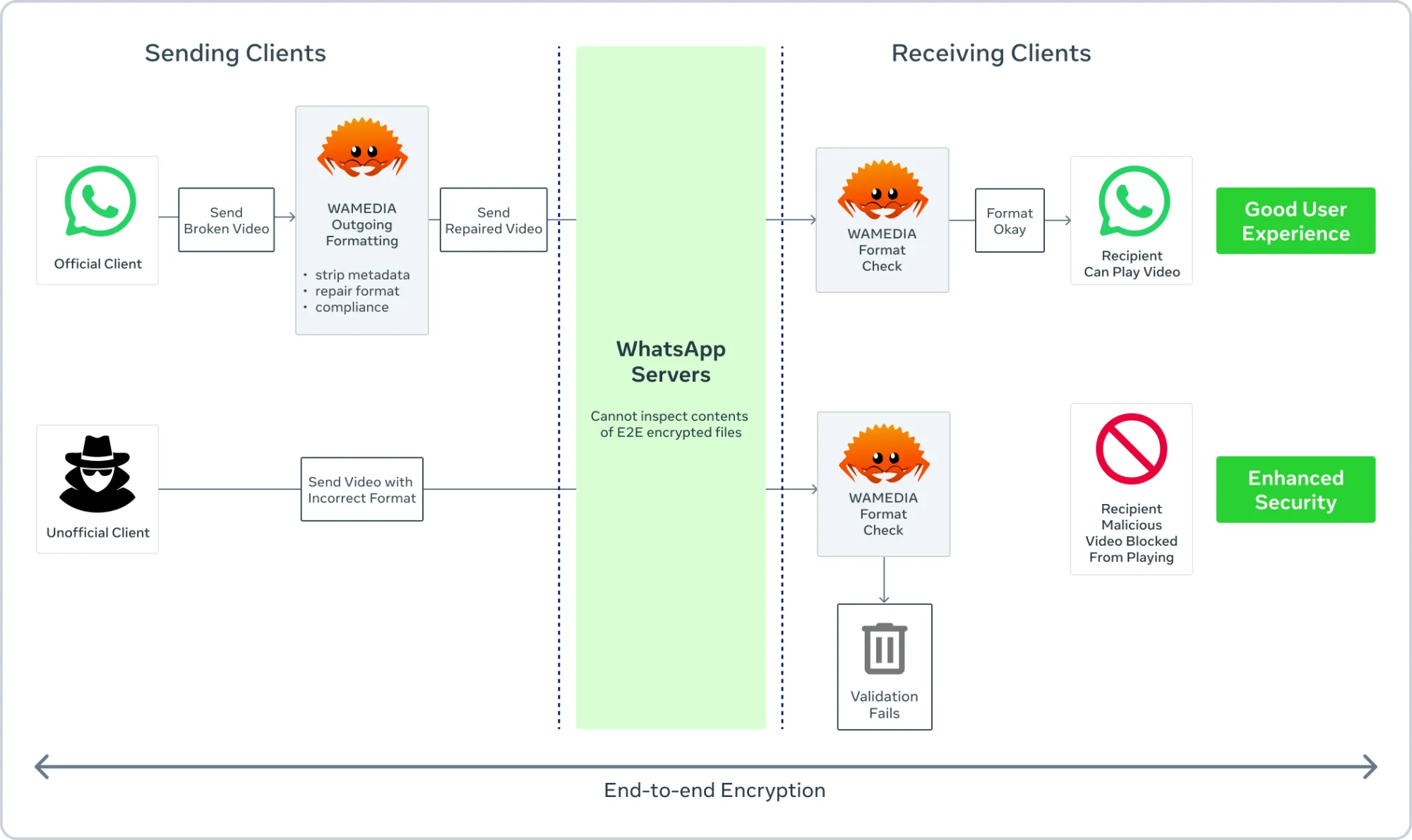
Previous exploits in WhatsApp such as the Stagefright vulnerability from 2015 exploited the OS-provided media parsing. wamedia acts as a filter of sorts to stop malformed and potentially malicious files before they are processed by those potentially vulnerable libraries.
The choice to develop it in Rust (in parallel with a C++ version in order to ensure compatibility) is an obvious one when you consider that memory safety vulnerabilities are a very common path of exploitation in software. Rust is a low-level memory safe programming language that excels in areas like systems programming that historically have been the realm of memory-unsafe C. WhatsApp were able to replace 160,000 lines of C++ code with just 90,000 lines of Rust code, with performance and memory usage advantages as well.
The WhatsApp team say that they're working on accelerating Rust adoption in WhatsApp in the coming years.
Given the many vulnerabilities that WhatsApp faces as one of the most popular messengers in the world, this is a good step I think toward protecting its users from the constant stream of exploits targeting everyday people. I hope to see a full Rust rewrite of WhatsApp at some point, and default-E2EE backups as well.

Community Discussion