Firefox 145 Boosts Privacy Amid AI Controversy, Android 16 QPR1 Source Code Released, Mullvad Shuts Down Leta Search Engine, and More
Our top stories this week:
- Firefox just got updated to version 145 which includes anti-fingerprinting protections by default.
- Firefox continues to add AI features to their browser despite backlash
- Android 16 QPR1 finally gets pushed to AOSP
- A leak reveals that the European Union
- X botches its security key transition, locking out thousands of passkey holders
- Google eases up on sideloading restrictions, exploring ways to allow advanced users to install non-verified apps
TWIP Live 🔴
Updates From The Team
This week we released a change log for all the changes that have been made to the website this month. Our volunteers and contributors have been making a lot of fixes and updates. Thank you to everyone that has contributed over the last month! However, there have been two big updates this month that you should be aware of.
DNS0.eu, the public, privacy-respecting DNS resolver fully hosted in the European Union, has been quietly shut down. The service was launched in 2023 by the founders of NextDNS; unfortunately, there was no formal announcement however they did confirm that the decision was made after efforts to secure continued funding failed. This DNS resolver has therefore been removed from the Privacy Guides website.

Mullvad has announced that their private search engine, Mullvad Leta, will be shutting down on the 27th of November. Leta allowed you to use Brave or Google's search indexes privately by proxying the requests. Mullvad stated the reason for discontinuing Leta was because: "The search industry continues to undergo big changes. Leta will not be able to follow and will likely become less useful over time." Because Mullvad Leta won't be available anymore it has been removed from the Privacy Guides website.

In terms of video projects, our team has been hard at work putting together a threat modelling course. One of the most common issues people face in our community is that they go too far with their privacy protections and don't consider probable threats, risks, and then decide what protections to put in place. This is quite a complex topic, so we're hoping to create a four-episode mini-course to guide people through the process.
Chat Control also continues to be a major issue in the EU. As of writing this newsletter, Chat Control has been pushed through a backdoor in the EU Parliament, and it is even worse than the original proposal. We remain committed as ever to cover this, and we have a video in the works so that we can spread the word and make sure people use their voices to oppose this indiscriminate mass surveillance proposal.
Sources
Mozilla's Firefox 145 is heeeeeere: Buffs up privacy, bloats AI
Mozilla has updated Firefox to version 145, with this update comes lots of additional features. This includes major privacy upgrades that address browser fingerprinting. Browser fingerprinting relies on unique configurations of your browser to create a user profile, such as your screen resolution, operating system, and hardware specifications. Overtime, this profile can be used to identify you as more data is collected.
Firefox claims these protections were carefully considered to avoid breaking websites; this means that the protections are less aggressive than many would like. However, this is still a positive development because most Firefox users use the default settings, which limits the general effectiveness of fingerprinting on the broader population. If you are looking for the best anti-fingerprinting measures, consider switching to Mullvad Browser and Tor Browser.
Firefox's documentation states the following changes:
- Random data is introduced to images generated in canvas elements when the website reads back the image. If a website merely renders data to the canvas element, it will render without alteration.
- The number of simultaneous touches your hardware supports is reported as either 0, 1, or 5 for all other values.
- Available Screen Resolution is reported as your Screen Resolution minus a height of 76 pixels.
- The number of processor cores is reported as either 4 (if you have 4 or fewer cores) or 8 (if you have more than 4 cores).
- Locally installed fonts will not be used to render text on a page.

Firefox adds AI Window, users want AI wall to keep it out
On November 13th, Ajit Varma, the VP and head of project management at Firefox, released a blog post detailing Firefox's new direction, announcing that they would be adding further AI integrations into the browser.
In the announcement, they said they are working on a new type of Firefox window that is available alongside standard and private browsing windows. It's called AI Window:
It’s a new, intelligent and user-controlled space we’re building in Firefox that lets you chat with an AI assistant and get help while you browse, all on your terms. - Ajit Varma
Mozilla claims that the feature will be entirely opt-in and that you will always be able to choose not to use the feature:
You decide when, how or whether to use it at all. You’ve already seen this approach in action through some of our latest features like the AI chatbot in the sidebar for desktop or Shake to Summarize on iOS. - Ajit Varma
It's certainly strange to see Mozilla pivoting Firefox towards AI integrations, clearly showing that they're abandoning their core mission of protecting their users’ privacy and security. It's unclear how this agentic AI browser integration will work yet; however, Mozilla does have a good track record of utilising privacy-respecting local AI models rather than sending data to third-party AI companies.
Including features not essential for standard browsing also expands the software’s attack surface, this is particularly concerning as so many sensitive operations are performed through a browser.

EU proposal mandates "risk mitigation" and age verification, de-facto brings back chat control
A leaked document dating to November 6th reveals that the EU is now considering a compromise proposal that essentially brings back chat control. Not only will it ban anonymous communication through mandatory age verification, it also implements a form of "digital house arrest" and requires "risk mitigation" for all service providers.
In a press release sent to Reclaim The Net, Patrick Breyer, Jurist and former Member of European Parliament, has lambasted the risk mitigation as a loophole that brings back chat control. Reclaim The Net reports: "Under the new text, providers would be obliged to take “all appropriate risk mitigation measures” to prevent abuse on their platforms.
While the Commission presents this as a flexible safety requirement, Breyer insists it is a loophole that could justify forcing companies to scan every private message, including those protected by end-to-end encryption. “The loophole renders the much-praised removal of detection orders worthless and negates their supposed voluntary nature,” he said. He warns that it could even lead to the introduction of “client-side scanning,” where users’ devices themselves perform surveillance before messages are sent."

The wait is over: Android 16 QPR1's source code is now available on AOSP
The Android 16 QPR1 feature update was released in early September for Google Pixel devices, however the open source code for the update was nowhere to be seen, this meant that GrapheneOS wasn't able to build a release with the new features, the update had one of the largest overhauls of Android's user interface with the introduction of Material You Expressive.
GrapheneOS could create security preview releases because they have access to the security patches through an OEM partner, meaning that users are protected against novel security threats. Android vendors receive security patches up to three months earlier, allowing GrapheneOS to ship the security fixes almost as soon as the Pixel receives them. However, they weren't able to update the userspace code because it was not yet pushed to the Android Open Source Project (AOSP).
There’s been a lot of speculation about Google’s decision to delay the release of the Android 16 QPR1 source code and whether they’re moving towards close sourcing. It’s good to see they’ve finally released it but GrapheneOS has warned on Mastodon that:
"The new security patch system being used by Android is confusing for users and bad for the security of anyone not using GrapheneOS with our security preview releases. We could have set the patch level string to 2025-11-01 in early September but in this case we didn't do that."

Elon Musk’s X botched its security key switchover, locking users out
X (formerly known as Twitter) has locked potentially thousands of users from their accounts because of a botched security key switchover. Since Elon Musk purchased Twitter in 2022, there has been a slow process of retiring the twitter.com domain and transitioning over to x.com. Passkeys using the FIDO2 standard are linked to website domains, meaning that users must manually reenroll their passkey to the new domain.
The platform has set a deadline of November 10 for passkey users to transition their security key. Given that X only gave a 15-day notice to users, we are not surprised by this debacle at all. Events like these are usually the fault of the service provider, not yours. After all, passkeys offer significant security benefits over traditional two-factor authentication methods such as TOTP and SMS/email.
Concerned that this may happen to you? Remain diligent on upcoming domain changes for the websites you use. If offered, make sure to retain backup codes and security question answers within a external safe.

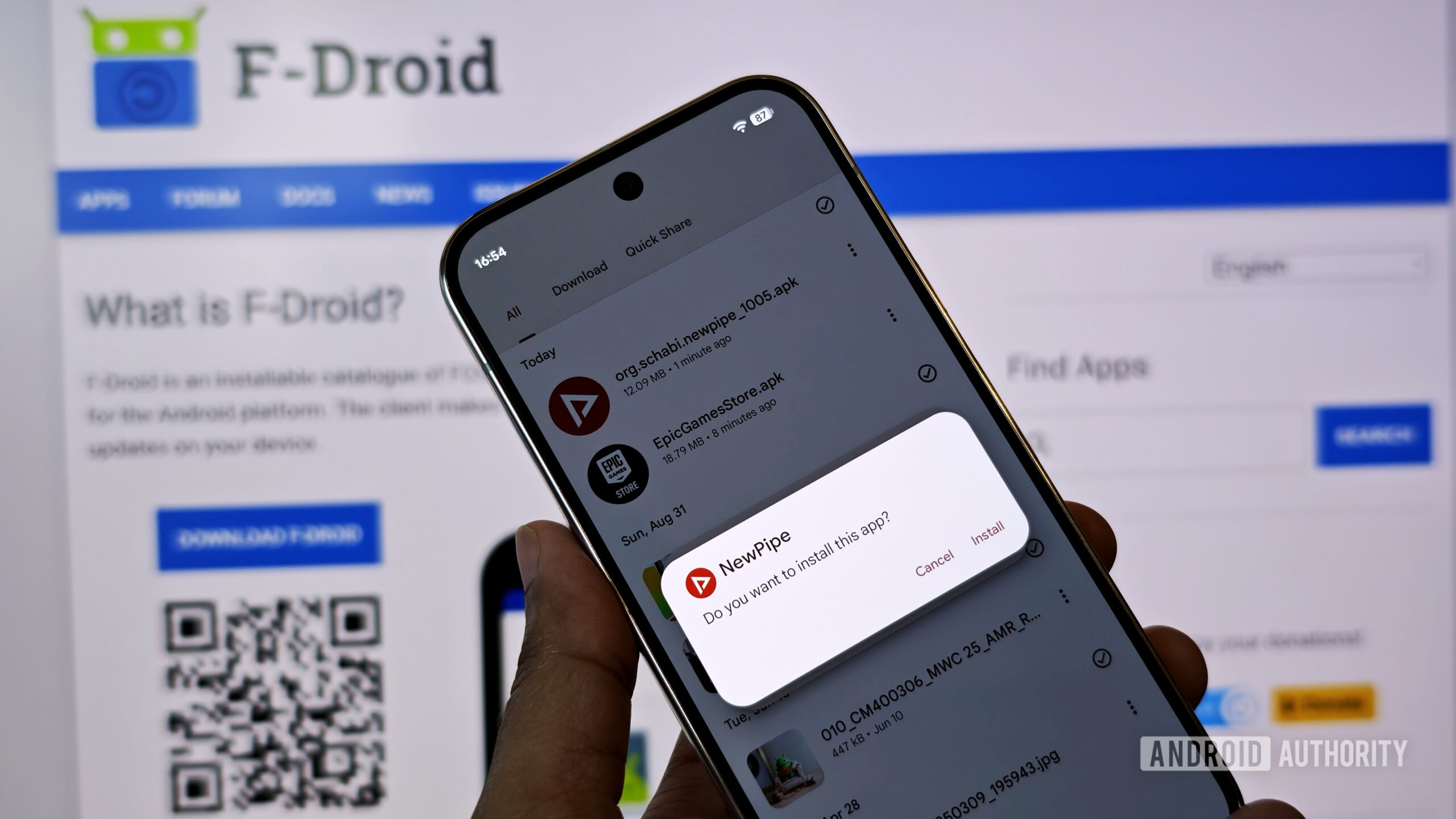
Google is easing up on Android's new sideloading restrictions

After gathering community feedback, Google is testing a new way for "experienced users" to install Android apps not verified under their upcoming Developer Verification Program. Although this compromise would make sideloading more difficult at first, it would ensure that low-knowledge users cannot accidentally install malware without learning about the dangers of doing so.
In their official development blog, Google writes:
Based on this feedback and our ongoing conversations with the community, we are building a new advanced flow that allows experienced users to accept the risks of installing software that isn't verified. We are designing this flow specifically to resist coercion, ensuring that users aren't tricked into bypassing these safety checks while under pressure from a scammer. It will also include clear warnings to ensure users fully understand the risks involved, but ultimately, it puts the choice in their hands. We are gathering early feedback on the design of this feature now and will share more details in the coming months.
Members on the community forum have speculated that sideloading may now appear in developer settings, with a pop-out alert explaining the security risks of doing so.
Forum Updates











